For his day job, Norman Shamas is the director of curriculum and pedagogy at an organization that helps people better use and understand technology. In his off-hours, he’s a rabble-rouser.
Based in Washington D.C., Shamas was an active organizer of the Michael Brown protests that confronted police violence. He and his colleagues organized the protests on Twitter with the hashtag #DCFerguson.
“People that use social media for organizing… should probably be aware that governments and potential adversaries monitor Twitter to have a leg up on any tactic and action,” warns Shamas. “The police were following #DCFerguson [on Twitter]; by the time we got to the shut down, the police had already started to redirect traffic.” [ed. note: a recent story in The Intercept details how U.S. authorities tracked Black Lives Matter activists after Ferguson]
Shamas goes on to elaborate that he and his partners hosted teach-ins at this time that were also visited by the police. This compromised the space, chilled the discussion and made advocacy impossible.
For advocates around the world, Shamas’ experience is not foreign. Whether you are an environmental advocate trying to stop an offshore oil platform from being built or a journalist with an extensive list of contacts in a totalitarian state, there’s a good chance you’ve experienced someone trying to access your communications or data.
This series provides an introduction on how to proactively protect data and improve online privacy. Through this process, this series never recommends a universal tool or procedure you can use to be secure, because that does not exist.
It’s not about the tool, says Allen Gunn, executive director at Aspiration, an organization that helps non-profits, foundations and activists improve their missions through technology. “It’s about the threat model.” This sentiment is echoed by Shauna Dillavou, the executive director at CommunityRED, a non-profit that trains journalists and activists about online security. “There needs to be a ritual of risk assessment. If you don’t know what you’re protecting yourself against, you’re just shooting in the dark.”
No matter who you are, where you are or what you do, protecting data and privacy is about habit formation and awareness, not apps and tools. Habit formation and awareness start with threat modeling. This process may be foreign at first, but by making it a part of your routine you can then assess what tools may be useful to you.
Threat modeling is foundational to digital security and privacy. It’s personal and subjective; it’s also not sexy. As Gunn puts it, “I feel like it’s telling people you have to grow your own organic vegetables.”
But like eating your veggies, digital security is important. In this piece, we’ll unpack the steps to creating a threat model and then apply them to a couple of hypothetical situations.
Create a Threat Assessment Now
The Electronic Frontier Foundation, an organization dedicated to defending civil liberties online, provides five questions that will help you arrive at your threat model.
1. What do you want to protect?
In online security parlance the things you want to protect are called assets. Assets are anything that you have that someone else might want. Examples may be call logs, emails, internal documents, or your physical hard drive. Write down anything and everything you have that could compromise yourself, your organization, or those on your contact lists. Remember, it’s likely not all of your documents, so be specific. Is that email to your mom about gardening actually damaging or worth encrypting?
2. Who are you protecting your assets from?
Once you know what you want to protect, ask from whom are you protecting it? There isn’t a single, omnipresent threat against all people’s data and privacy. This isn’t 1984. So, ask yourself questions like, who is your adversary? Who would want to collect your data? Who would want to listen to your conversations? The threat will always be unique to you, your data and your circumstance.
3. How likely is it that you will need to protect your assets?
Now that you know what you’re trying to protect and whom you are protecting it from, how likely is the threat to materialize? This is a hard part to threat modeling. Do you know the capability of your adversary? This may take research into both the adversary and your vulnerability. Further, how likely is it that the adversary will make a move on your data or hardware?
This process is hard and in many ways uncertain, says Nick Sera-Leyva, Human Rights and Training Programs Manager at Internews, an organization that promotes local-media worldwide. “The threats you are worried about might not immediately materialize. It’s not like touching a hot stove where you figure out [the harm] immediately. With digital security, you may never realize you are the target of an attack, you might not know the consequence until days, weeks or months later.”
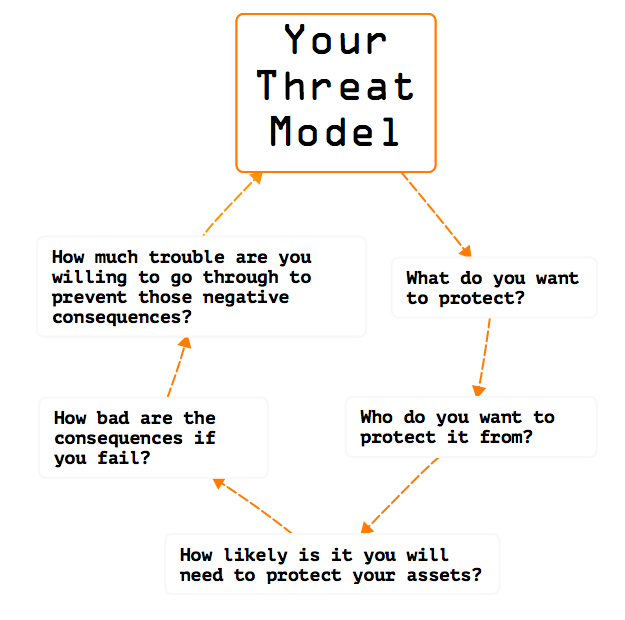
4. How bad are the consequences if you fail?
At the beginning of this article, you were introduced to Norman Shamas. His online, public advocacy meant that the police knew about his protests and teach-ins, diminishing the value of his work. Under the same circumstances, but in a place like Azerbaijan, the risk could be arrest, false imprisonment and trumped-up criminal charges. This question gets to the heart of whom you are protecting your data from, their power and what kind of liability your conversations and data create.
5. How much trouble are you willing to go through in order to prevent those negative consequences?
Doing nothing about your digital security shouldn’t be treated as an option says Gunn. That’s why acknowledging your threats is only half of the battle. The last step to threat modeling is asking what are you willing to do about it? This is a personal aspect of threat modeling. Not everyone is going to see the same value in the same assets, nor will everyone be willing or capable of taking certain protective measures.
Security comes with costs. “Efficiency is lost with security. Software updates, new products, new updates, new threats all take time to learn about and implement,” says Gunn. As examples, he points to Skype and Google Docs as two platforms that trade high-utility for low-security.
In the next article, we’ll talk about some steps and tools that may be useful to you depending on your threat model. For now, however, let’s see if you can create a threat model for the examples below.
Some Scenarios to Consider
Now that you have some threat assessment guidelines, let’s try out a couple examples:
You are going on a picnic with your family. The park you are visiting is known to have an incompetent staff and a very cunning bear and cub. Many families have complained about their picnic baskets being stolen by these two, dastardly bears. Now, scroll up and look at those five questions. What’s your threat model for this situation?
The assets are the picnic basket, its contents, and perhaps your family’s personal safety. The bear and his cub create the threat to these edible assets. Judging by other reports, the likeliness of having this basket stolen is high. If you fail to protect the basket your family’s trip to the park will be negatively affected and the chances of a hangry partner or child are also high. At this point, you can start looking at options to protect your picnic basket. Will a lock do? A tether? A decoy basket? Accepting a high probability of picnic basket theft, perhaps you leave the picnic basket at home. It’s about what works for you and your situation.
You are an environmental activist in a nation with a hostile government and a lazy but intrusive police service; the government lacks digital sophistication. You operate either on your smartphone or your office’s computer. Again, scroll up and apply those five questions to this hypothetical situation. What’s your threat model?
Some assets you may want to protect are plans and internal documents about your activism, contact lists, calendars, and metadata created through your smartphone like your location. Your main threat seems to be the government and its agents. If the government goes after you, but lacks technical sophistication, maybe snatching your smartphone or computer seems more likely than a cyber attack. If the police are in fact lazy, maybe the chances of them robbing you are low. In this case, you may want to use strong passphrases, encrypt your hard drive, and make sure you have encrypted backups in safe locations (all things we’ll discuss in this next article). If the physical location of your data is at risk, you might want to look at stronger physical security like locks, alarms and cameras.
Categories:
safety and security





